
NetID+ enhances the security of your UA NetID by using technology from Duo Security which leverages your device (e.g., smartphone or tablet) to verify your identity. This prevents anyone but you from accessing applications and services secured with NetID+, even if they know your password.
You can complete the second step in the login process in many ways, including:
Passwords are becoming increasingly easy to compromise. They can often be stolen, guessed, and hacked — you might not even know who else has your password and is accessing your account. NetID+ adds a second layer of security to your account to make sure that your account stays safe, even if someone else knows your password — and you'll be alerted right away (on your phone) if someone does know your password and tries to log in with it. This second factor of authentication is separate and independent from your UA NetID username and password step — Duo Security never sees your password.
Apple iOS and Android devices are supported. See Supported Devices for information on installing and using the Duo Security app on various platforms.
There are many other methods available if you don't use a smart device (phone/tablet). One-time passcodes (OTP) can be sent to any phone capable of receiving SMS text messages. Additionally, Yubikey or Feitian OTP hardware tokens can be enrolled and used with NetID+.
Search your device’s app store for "Duo Mobile". It is available on Android and Apple iOS platforms.
Duo Mobile is an app that allows you to generate passcodes that you can use for NetID+. It is available on Android and Apple iOS platforms. The Duo Mobile app can use Duo Push functionality. When you get to the second step in the NetID+ process, your Duo Mobile app will alert you that somebody is trying to log in with your UA NetID. You can approve or reject the login on your device.
You can configure phones that can be used as Lifeline devices when your regular devices are unavailable. A Lifeline phone usually belongs to somebody you trust and with whom you can easily communicate.
For example, if you lose your phone and need to use NetID+, you can log in to the NetID+ management site using just your NetID and password. After you log in, you will see an option to “Use a Lifeline”. When you choose the lifeline you would like to use (you may have more than one configured) , a verification code will be sent by text message or a phone call to that phone. The owner of that phone can communicate the code to you, and you can enter the code into this application to produce a list of ten bypass codes. Those bypass codes will allow you to complete NetID+. After completing NetID+ login, you can go to the “Manage your Account” page to manage your NetID+ devices. You can remove your lost phone and configure a new device for future logins. You can also print out more bypass codes.
If your phone battery dies, you change your phone number, or you otherwise do not have access to any way to authenticate, call the 24/7 IT Support Center at (520) 626-8324 (TECH). The 24/7 tech will verify your identity and provide you with some NetID+ bypass codes.
Add as many devices as you can to give yourself more options. Create a Lifeline, as well, as another backup.
Yes. You can register any number of devices via the NetID+ “Manage your Account” page (under “Add a Device”).
Any type of passcode can be used anytime you see a “Passcode” field on the NetID+ login page. Here are the type of passcodes available to you, and how they can be generated:
NetID+ supports 2 types of hardware tokens:
YubikeyYou can use any of the Yubikey 5 Series devices with NetID+. You can purchase Yubikey Series 5 devices from directly from Yubico. Please follow instructions on the Yubico website for downloading configuration software and configuring your Yubikey.
Downloading the Yubikey Personalization Tool:
You can retrieve the Yubikey Manager installer for Mac OS X, Windows and Linux from https://www.yubico.com/products/services-software/download/yubikey-manager/ (under “Cross-Platform Tool”).
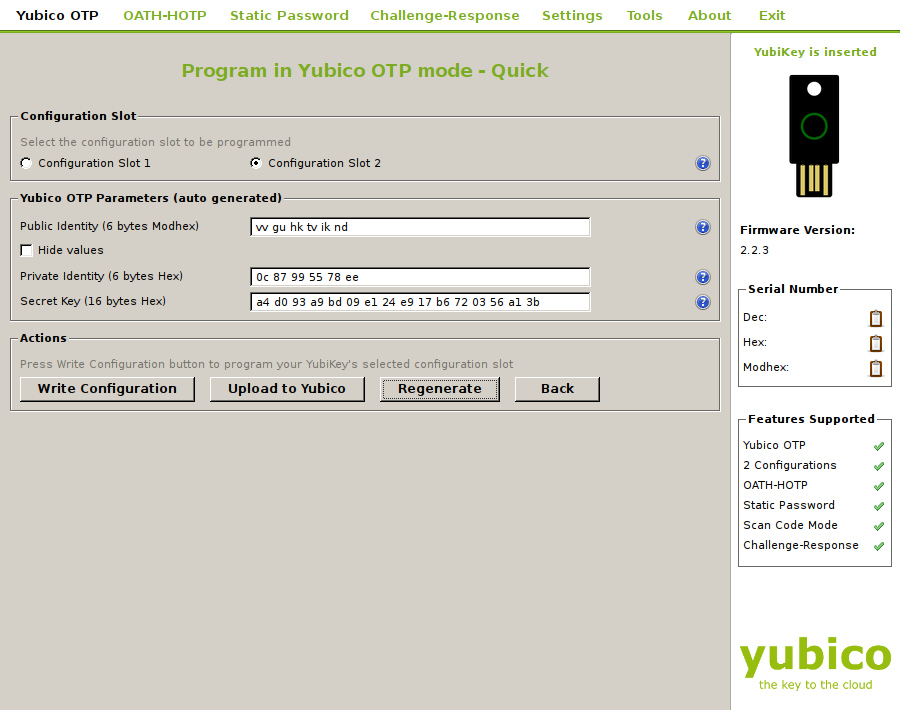
If you are already using this YubiKey with an existing service, the following steps will overwrite the stored secret for that service. You should also realize that every time you open the Yubico OTP tab, it generates a new Public Identity, Private Identity, and Secret Key, but that these are not written to the token unless you actually click Write Configuration. There is no way to read your existing Public Identity, Private Identity, and Secret Key off the token once it has been written.
Each YubiKey has two slots. The first slot is used to generate the passcode when the YubiKey button is touched for between 0.3 and 1.5 seconds and released. The second slot is used if the button is touched between 2 and 5 seconds. When the YubiKey is shipped its first configuration slot is factory programmed for the YubiCloud OTP service and the second configuration slot is blank.
To create or overwrite a slot’s configuration:
The OTP c100 is a low-cost, small key-chain authentication token. It provides a one-time password (OTP) by clicking a button on the device. Each OTP is only valid until the next button click. Battery life on the OTP c100 is between 3-5 years (depending on use); once the battery dies, the token must be replaced.
Feitian OTP tokens may be purchased directly from Feitian.
You will be asked to select "seed format" and "seed encryption" values, and provide a "seed delivery email" (see illustration below).
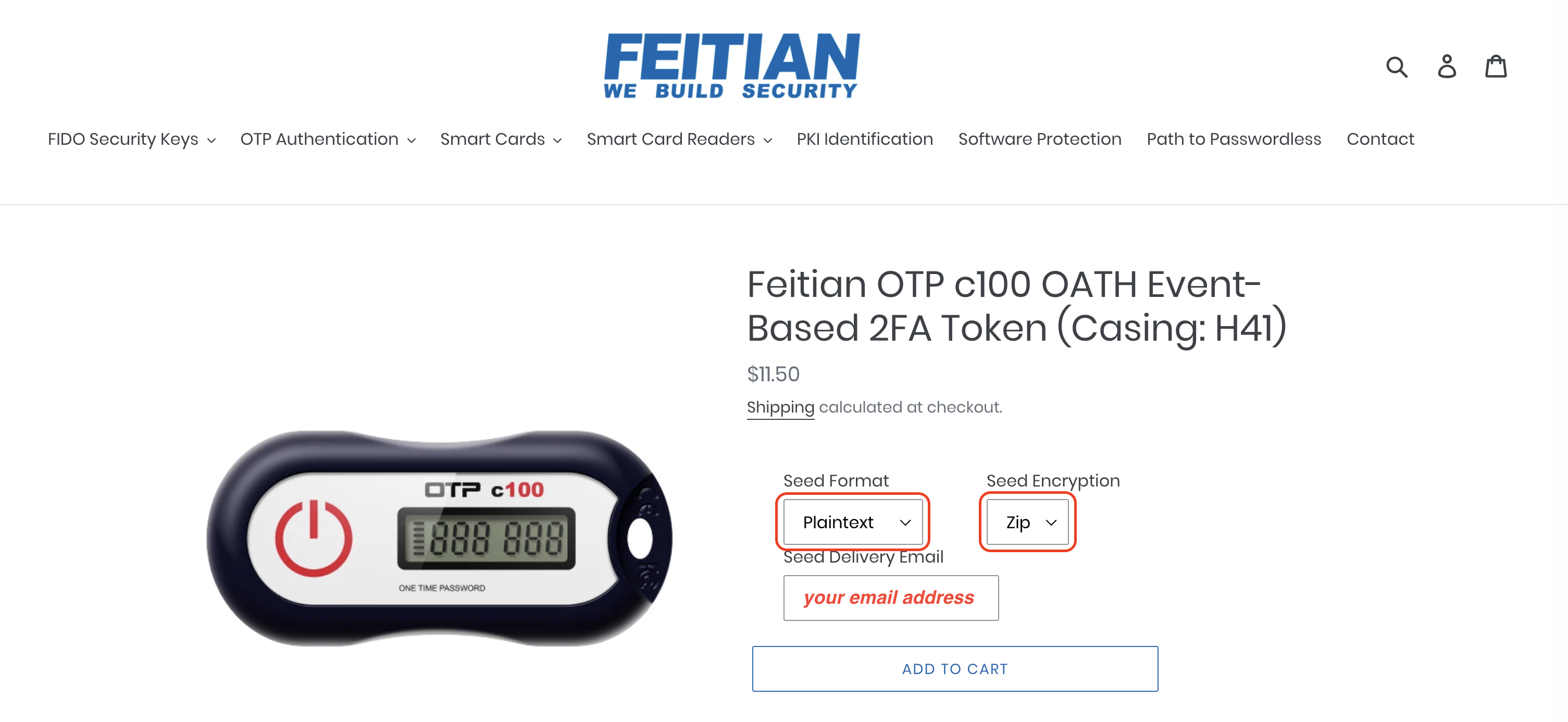
Use the default values on the form for "seed format" and "seed encryption", and use your email address for the "seed delivery email". Feitian will send you 2 emails, one (subject "otp info") containing a zip file, and another (subject "unzip info") with a password that will be needed to decrypt the zip file when you attempt to open it. DO NOT DELETE OR LOSE THESE EMAILS! Your OTP c100 token will be unusable without the data contained in the zip file.
Before enrolling your token, use the password contained in the "unzip info" email to unzip the attachment contained in the "otp info" email, then open the resulting text file in an editor. The file will contain two values, separated by a space. The first value is the serial number of your token (also printed on the back of the token) — enter this in the "Serial Number" field on the OTP c100 enrollment form. The second value is the token's "seed" — enter this in the "Seed Value" field on the OTP c100 enrollment form.
If you generate 20 or more codes on your OTP c100 token without authenticating, your token will need to be re-synchronized with Duo. Note that a token can only be re-synchronized if it is off from the server by less than 1000 events (button presses) — therefore it is not advisable to repeatedly press the button on your token if you are not actually performing an authentication.
To re-synchronize your token, attempt to login to a WebAuth-protected application, using your token for the 2nd factor. You will receive "invalid passcode" errors the first 2 times you attempt to login, but the third attempt will be successful.
You can use the “Manage your Account” page to generate new printable single-use bypass codes, or register additional devices. You can also configure your self-service support or "lifeline" options. Access to the “Manage your Account” page is itself protected with NetID+.
We recommend that anyone who travels internationally, and needs to log into UA systems with NetID+, generate a list of NetID+ Bypass Codes and register at least one NetID+ Lifeline. NetID Bypass Codes are generated in batches of 10 via the NetID+ self-service site; each code is good for one login, and you can generate more at any time. Your last bypass code should be used to generate a new batch of bypass codes, if you do not have access to any other enrolled device.
Note: If you travel internationally and use SMS passcodes as your primary NetID+ authentication mechanism, the text messages you receive may incur substantial roaming charges. If you have a Google Voice account tied to an external Gmail account (i.e., @gmail.com, not @email.arizona.edu), you can set that up with NetID+ as an SMS-capable phone and configure it to deliver incoming SMS messages to your Gmail mailbox.
If you expect to travel internationally and cannot set up Duo Mobile as your NetID+ authentication method, bypass codes, a Yubikey hardware token, or the aforementioned Google Voice approach are your best alternatives.
Your password is reusable, so if someone steals it, they can keep using that password with your account over and over again. Bypass codes can only be used once and are easily invalidated if necessary. NetID+ is based on the idea of 1) something you know (your password) and 2) something you have (your smartphone or token, or your printed codes).
You should also store your bypass codes in your wallet. You're likely to always know where your wallet is and immediately notice when it's missing. That way, you can quickly invalidate your codes (by simply generating a new batch, via the “Print Bypass Codes” button on the “Manage your Account” page) if your wallet is stolen or lost. Also, even if it is lost, the person who steals or finds it only has your bypass codes, and can't log in without your password. Don't write down your password!
After reinstalling the Duo Mobile app, access the NetID+ “Manage your Account” page, using an SMS code to authenticate (since Duo Push needs to be re-activated). Once you’ve logged-in, click the yellow “Re-activate” button on the affected device, and follow the on-screen instructions.
Typically, SMS messages are delivered within a few minutes, but delivery delays can happen depending on the cell carrier's infrastructure. You can always request more passcodes via the “send more” link (under the “Passcode” option on the NetID+ form). You can also generate a passcode via the Duo Mobile app on your device.
Passcodes must be used in the sequence in which they are presented. If you have previously received SMS passcodes, there should be a message under the “Passcode” option on the NetID+ form indicating the starting digit of the next passcode to use (e.g., “Next SMS passcode starts with 2 (send more)”). Also, be aware that requesting a new set of passcodes (via the “send more” link) automatically invalidates any previous passcodes you have received.
No, you can't use Google Authenticator with NetID+. However, you can store Google's two-step verification credentials (as well as any other site using TOTP, like GitHub, Dropbox, etc) in the Duo Mobile app.
Info on adding third-party accounts to Duo Mobile can be found at http://guide.duosecurity.com/third-party-accounts.